|
|
Evidence in Federated Distributed Systems
Overview
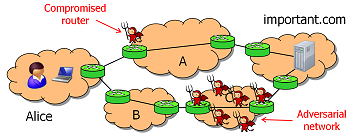 There is an increasing trend towards federated distributed systems, i.e., systems
that are operated jointly by multiple different organizations or individuals.
The interests of the participants in such a system are often highly diverse
and/or in conflict with one another; for example, participants may be business
competitors or based in hostile nations. Thus, federated systems are inherently
vulnerable to insider attacks: the participants can try to subvert the system,
exploit it for their own benefit, or attack other participants.
There is an increasing trend towards federated distributed systems, i.e., systems
that are operated jointly by multiple different organizations or individuals.
The interests of the participants in such a system are often highly diverse
and/or in conflict with one another; for example, participants may be business
competitors or based in hostile nations. Thus, federated systems are inherently
vulnerable to insider attacks: the participants can try to subvert the system,
exploit it for their own benefit, or attack other participants.
However, the participants in a federated system are typically connected in the
'offline world' as well, e.g., through social networks or business relationships.
This context can be leveraged to handle misbehavior through well-known, time-tested
techniques like accountability and transparency. For example, if one participant
can detect and prove that another participant has misbehaved, she can sue that
participant for breach of contract.
The goal of this project is to develop a key technology for enabling this approach,
namely a reliable and general way to generate and verify evidence of misbehavior
in federated systems. We study the fundamental tradeoffs, requirements, and inherent
costs of creating evidence, we develop new algorithms for efficiently supporting
different kinds of evidence, and we evaluate these algorithms in the
context of practical systems.
Software
PeerReview library: v1.1.2
Publications
- Fault Tolerance and the Five-Second Rule
Ang Chen, Hanjun Xiao, Andreas Haeberlen, and Linh Thi Xuan Phan
To appear at: 15th Workshop on Hot
Topics in Operating Systems (HotOS XV),
Kartause Ittingen, Switzerland, May 2015.
[PDF] [BibTex]
- Detecting Covert Timing Channels with Time-Deterministic Replay
Ang Chen, W. Brad Moore, Hanjun Xiao, Andreas Haeberlen, Linh Thi Xuan Phan, Micah Sherr, and Wenchao Zhou
11th USENIX Symposium on
Operating Systems Design and Implementation (OSDI '14),
Broomfield, CO, October 2014.
[PDF] [BibTex]
- Diagnosing Missing Events in Distributed Systems with Negative Provenance
Yang Wu, Mingchen Zhao, Andreas Haeberlen, Wenchao Zhou, and Boon Thau Loo
Proceedings of ACM SIGCOMM 2014, Chicago, IL, August 2014.
[PDF] [BibTex] [Technical report] [Yang's slides]
- Let SDN be your eyes: Secure Forensics in Data Center Networks
Adam Bates, Kevin Butler, Andreas Haeberlen, Micah Sherr, and Wenchao Zhou
NDSS Workshop on
Security of Emerging Network Technologies (SENT '14), San Diego,
CA, February 2014.
[PDF] [BibTex]
- Answering Why-Not Queries in Software-Defined Networks with
Negative Provenance
Yang Wu, Andreas Haeberlen, Wenchao Zhou, and Boon Thau Loo
12th ACM Workshop
on Hot Topics in Networks (HotNets-XII), College Park, MD,
November 2013.
[PDF] [BibTex]
- Towards Privacy-Preserving Fault Detection
Antonis Papadimitriou, Mingchen Zhao, and Andreas Haeberlen
9th Workshop on Hot Topics in
Dependable Systems (HotDep '13), Farmington, PA, November 2013.
[PDF] [BibTex]
- Private and Verifiable Interdomain Routing Decisions
Mingchen Zhao, Wenchao Zhou, Alexander J. T. Gurney, Andreas Haeberlen, Micah Sherr,
and Boon Thau Loo
Proceedings of ACM SIGCOMM 2012, Helsinki, Finland, August 2012
[PDF] [BibTex] [Technical report]
- Reliable Client Accounting for Hybrid Content-Distribution Networks
Paarijaat Aditya, Mingchen Zhao, Yin Lin, Andreas Haeberlen, Peter Druschel, Bruce Maggs, Bill Wishon
9th USENIX Symposium on Networked Systems Design and Implementation (NSDI' 12), San Jose, CA, April 2012
[PDF] [BibTex]
- Having your Cake and Eating it too: Routing Security with Privacy Protections
Alexander J. T. Gurney, Andreas Haeberlen, Wenchao Zhou, Micah Sherr, and Boon Thau Loo
10th ACM Workshop on Hot Topics in Networks
(HotNets-X), Cambridge, MA, November 2011.
[PDF] [BibTex] [Slides]
- Secure Network Provenance
Wenchao Zhou, Qiong Fei, Arjun Narayan, Andreas Haeberlen, Boon Thau Loo, and Micah Sherr
23rd ACM Symposium on Operating Systems Principles
(SOSP '11), Cascais, Portugal, October 2011.
[PDF] [BibTex] [Technical report]
- Differential Privacy Under Fire
Andreas Haeberlen, Benjamin C. Pierce, and Arjun Narayan
20th USENIX Security Symposium, San Francisco, CA, August 2011.
[PDF] [BibTex] [Slides] [Software]
- Challenges in Experimenting with Botnet Detection Systems
Adam J. Aviv and Andreas Haeberlen
4th USENIX Workshop on Cyber Security Experimentation and Test (CSET '11), San Francisco, CA, August 2011.
[PDF] [BibTex]
- TAP: Time-aware Provenance for Distributed Systems
Wenchao Zhou, Ling Ding, Andreas Haeberlen, Zachary Ives, and Boon Thau Loo
3rd USENIX Workshop on the Theory and Practice of Provenance (TaPP '11), Heraklion, Greece, June 2011.
[PDF] [BibTex]
- NetTrails: A Declarative Platform for Maintaining and Querying Provenance in Distributed Systems
Wenchao Zhou, Qiong Fei, Shengzhi Sun, Tao Tao, Andreas Haeberlen, Zachary Ives, Boon Thau Loo, and Micah Sherr
Demo. ACM SIGMOD International Conference on Management of Data (SIGMOD '11 demo), Athens, Greece, June 2011.
[PDF] [BibTex]
Contributors
Faculty:
Andreas Haeberlen
Students:
Mingchen Zhao
Arjun Narayan
Alumni:
Prakashkumar Thiagarajan
Funding
This work is funded by the National Science Foundation
under the Trustworthy
Computing program (grant number CNS-1054229). Any opinions, findings, and conclusions or
recommendations expressed in this material are those of the author(s) and do not necessarily
reflect the views of the National Science Foundation.
| |
|
 There is an increasing trend towards federated distributed systems, i.e., systems
that are operated jointly by multiple different organizations or individuals.
The interests of the participants in such a system are often highly diverse
and/or in conflict with one another; for example, participants may be business
competitors or based in hostile nations. Thus, federated systems are inherently
vulnerable to insider attacks: the participants can try to subvert the system,
exploit it for their own benefit, or attack other participants.
There is an increasing trend towards federated distributed systems, i.e., systems
that are operated jointly by multiple different organizations or individuals.
The interests of the participants in such a system are often highly diverse
and/or in conflict with one another; for example, participants may be business
competitors or based in hostile nations. Thus, federated systems are inherently
vulnerable to insider attacks: the participants can try to subvert the system,
exploit it for their own benefit, or attack other participants.